- A Windows Azure subscription (duh)
- A working PKI Infrastructure
- 2 (a .cer and a .pfx) certificates to talk to the Management service of Windows Azure
- A certificate (the .cer) added to the Management service of Windows Azure
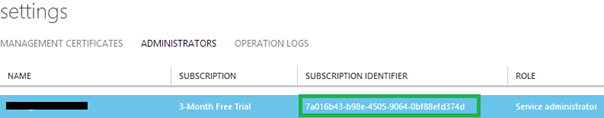
- Your Windows Azure Subscription ID. This can be found on the Management Portal of Windows Azure.
- And well, uh SCCM 2012 SP1 ;-)
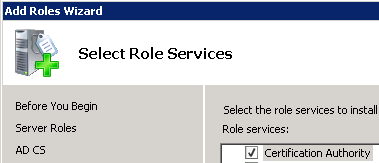
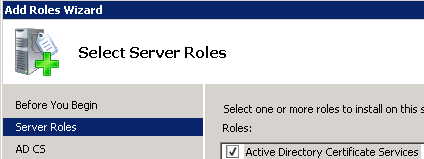 Certificate Authority:
Certificate Authority:
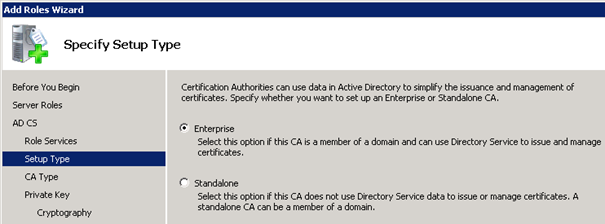
 Enterprise:
Enterprise:
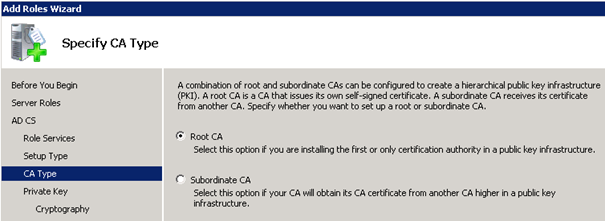
 Root CA:
Root CA:
 New private key:
New private key:
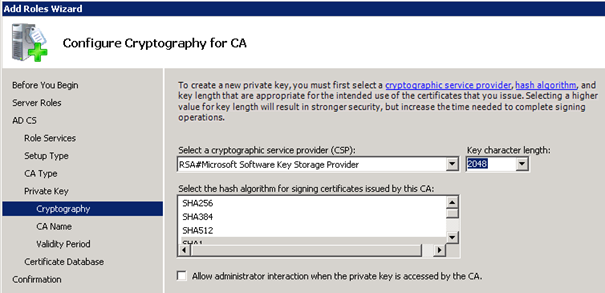
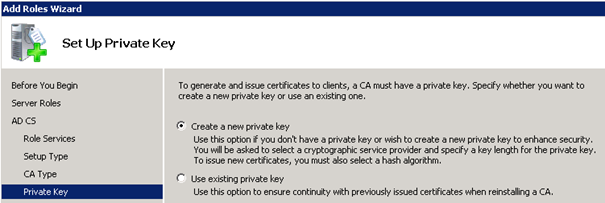 Select 2048 for Key character length:
Select 2048 for Key character length:
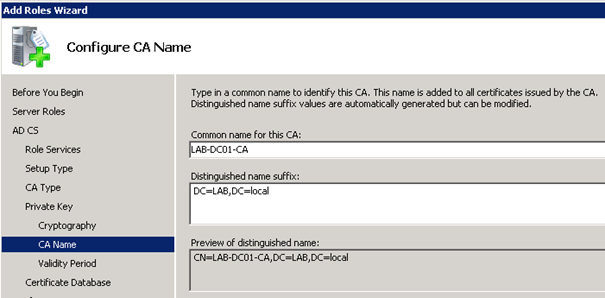
 CA Name:
CA Name:
 Validity period (I don't think my lab will last this long ;-))
Validity period (I don't think my lab will last this long ;-))
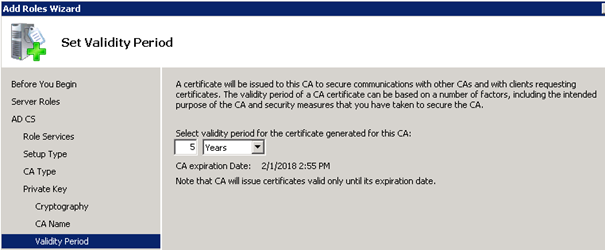 Now Install the CA.
Deploy the Certificate
So that's up and running, now for the fun part.
Microsoft has some good info on what certificates you need.
Source:
Now Install the CA.
Deploy the Certificate
So that's up and running, now for the fun part.
Microsoft has some good info on what certificates you need.
Source:
- Deployment of the PKI Certificates for Configuration Manager:
- PKI Certificate Requirements for Configuration Manager:
http://technet.microsoft.com/en-us/library/gg699362.aspx
We will go from there.- Create a Security Group that contains the member servers to install System Center 2012 Configuration Manager SP1 primary site servers that will manage cloud-based distribution points.
- On your Certificate Authority (CA) server go to the console and right-click Certificate Templates, choose Manage.
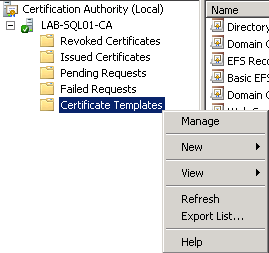
- Right-click the entry that displays Web Server in the column Template Display Name, and then click Duplicate Template.

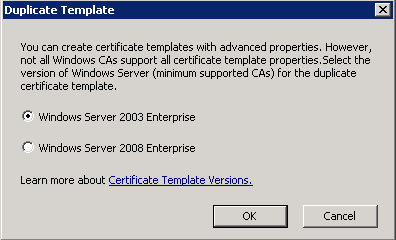
- Select Windows Server 2003, Enterprise Edition
- On the General tab enter a name (ConfigMgr Cloud-Based Distribution Point Certificate)
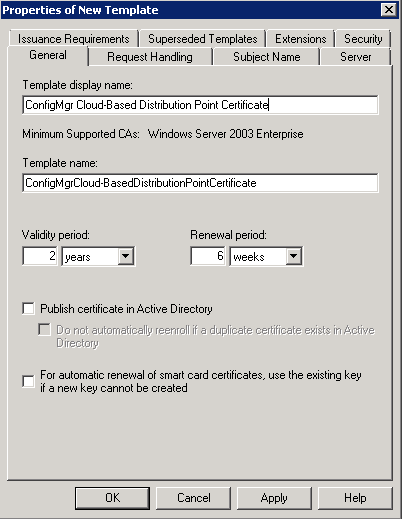
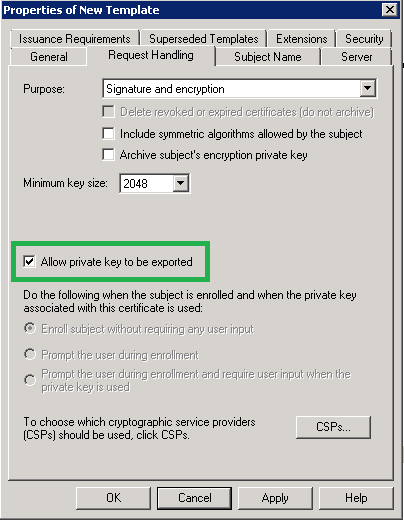
- On the Request Handling tab – Allow private key to be exported.
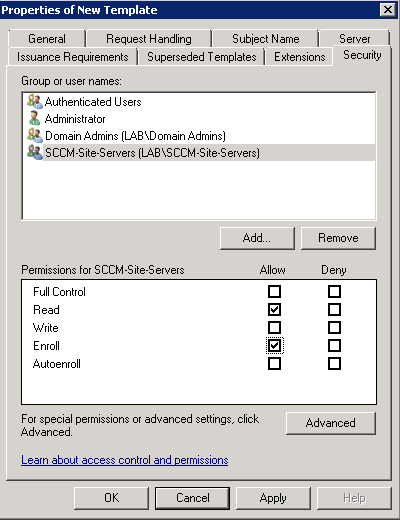
- Security tab – Remove Enroll for Enterprise Admins and Add your Security Group.
- Click OK and close the Template console.
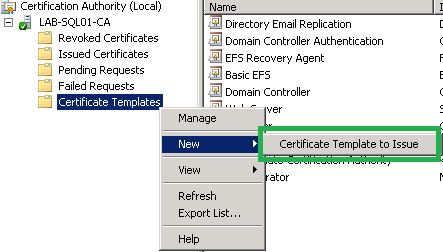
- Right-click Certificate Templates, New – Certificate Template to Issue.
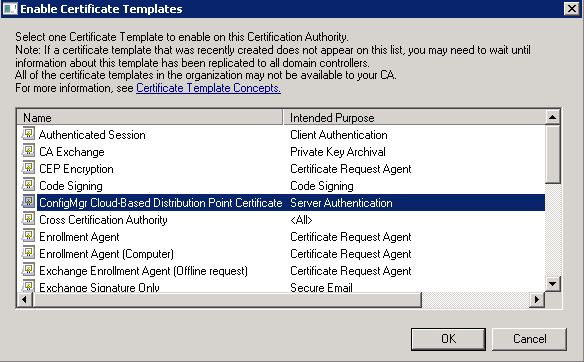
- Select your Template and select OK.
- Go to your site server.
- Open up a MMC and add Certificates – Local computer as snap-in.
- Go to Personal and in All Tasks select Request New Certificate.
 Now you have to enter some information:
Now you have to enter some information:
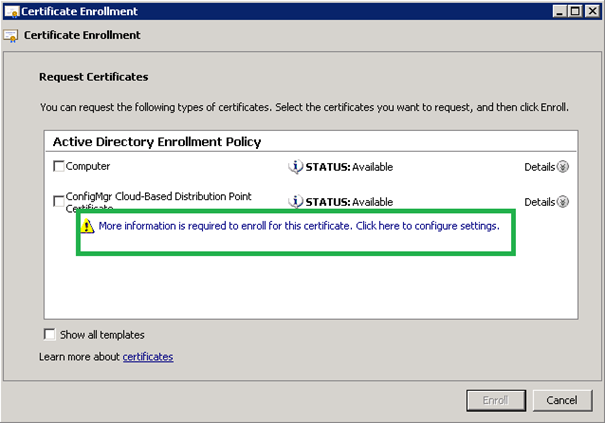 The info you need for Windows Azure is:
- the name of your Windows Azure Cloud Distribution Point
The info you need for Windows Azure is:
- the name of your Windows Azure Cloud Distribution Point
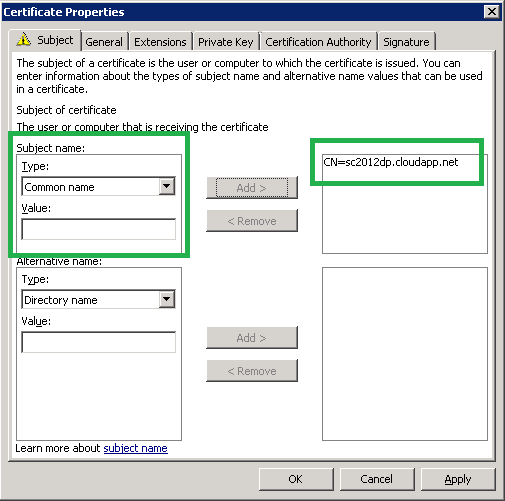
- Select and Enroll.
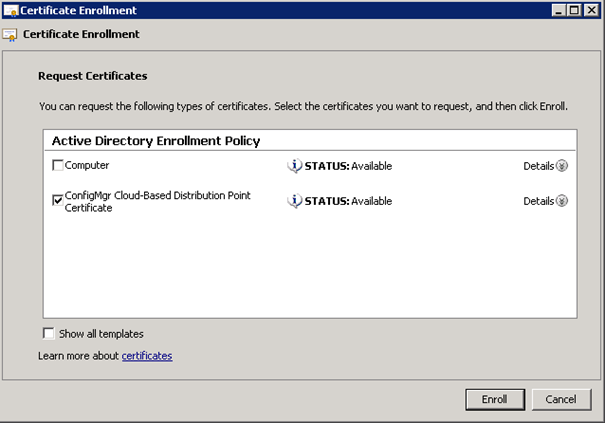
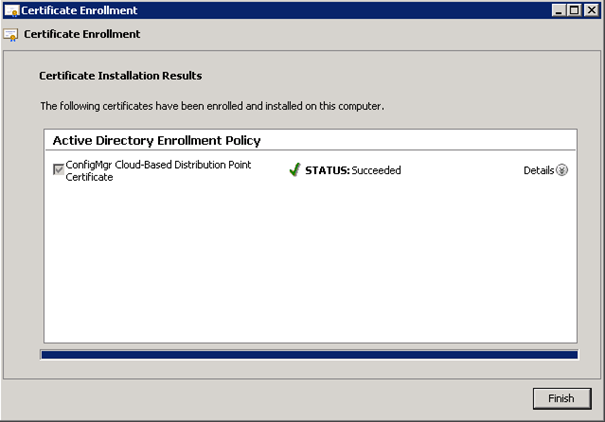
- Enrollment successful.
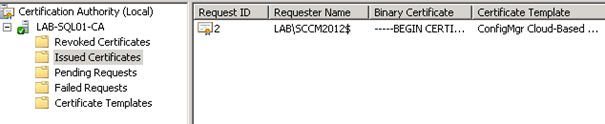
- The Certificate will be visible in the CA console under Issued Certificates.
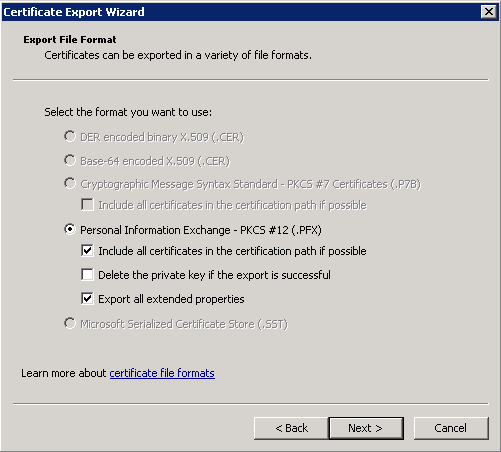
- Without the Private Key:
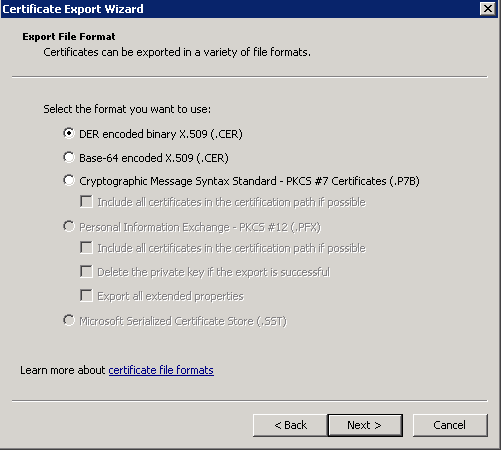
- And with the Private Key:

No comments:
Post a Comment