- Client Certificate
- Web Server Certificate
- Client certificate for Distribution Points
Client Certificate
On the Certificate Authority (CA) server open up your CA and Duplicate Template.
The template you need for this is the Workstation Authentication.
Make sure to select 'Windows Server 2003 Enterprise' as 'Windows Server 2008 Enterprise' is NOT supported by ConfigMgr 2012 SP1!
On the security tab select 'Read' and 'Autoenroll' for Domain Computers, do not clear 'Enroll'.
Back in the CA console, right-click Certificate Templates, New and Certificate Template to Issue. Choose your Client Certificate.
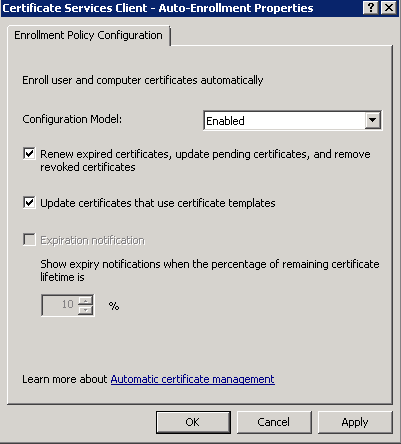
 Auto-enrollment of the Client Certificate
For auto-enrollment use a Group Policy Object (GPO).
Best practice is to use a separate GPO for the auto-enrollment.
In the Group Policy Management console, Create a GPO in this domain, and Link it here.
(be sure to point to the right Organizational Unit (OU)).
Now go to Computer Configuration – Policies – Windows Settings – Security Settings – Public Key Policies.
Auto-enrollment of the Client Certificate
For auto-enrollment use a Group Policy Object (GPO).
Best practice is to use a separate GPO for the auto-enrollment.
In the Group Policy Management console, Create a GPO in this domain, and Link it here.
(be sure to point to the right Organizational Unit (OU)).
Now go to Computer Configuration – Policies – Windows Settings – Security Settings – Public Key Policies.
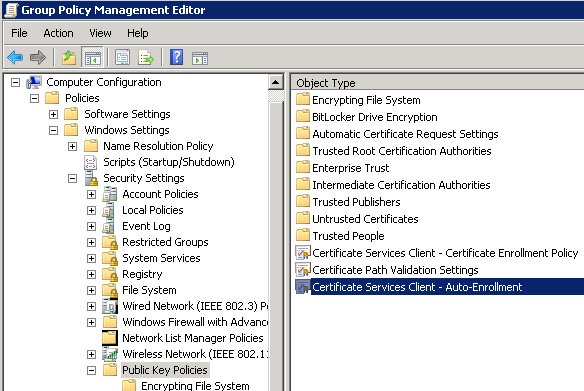 Right-click and Enable auto-enrollment:
Right-click and Enable auto-enrollment:
 Web Server Certificate
On the Certificate Authority (CA) server open up your CA and Duplicate Template.
The template you need for this is the Web Server.
Make sure to select 'Windows Server 2003 Enterprise' as 'Windows Server 2008 Enterprise' is NOT supported by ConfigMgr 2012 SP1!
On the security tab select 'Read' and 'Enroll' for your SCCM Site (IIS) Server(s), clear 'Enroll' for Enterprise Admins.
On the Subject Name tab be sure the Supply in the request is selected.
Back in the CA console, right-click Certificate Templates, New and Certificate Template to Issue. Choose your ConfigMgr Web Server Certificate.
Web Server Certificate
On the Certificate Authority (CA) server open up your CA and Duplicate Template.
The template you need for this is the Web Server.
Make sure to select 'Windows Server 2003 Enterprise' as 'Windows Server 2008 Enterprise' is NOT supported by ConfigMgr 2012 SP1!
On the security tab select 'Read' and 'Enroll' for your SCCM Site (IIS) Server(s), clear 'Enroll' for Enterprise Admins.
On the Subject Name tab be sure the Supply in the request is selected.
Back in the CA console, right-click Certificate Templates, New and Certificate Template to Issue. Choose your ConfigMgr Web Server Certificate.
 Enrollment of the ConfigMgr Web Server Certificate
Open a MMC and add the Certificate snapin for Local Computer.
Right-click Certificates and Request New Certificate. Select the ConfigMgr Web Server Certificate you created.
Select More information is required to enroll for this certificate. Click here to configure settings.
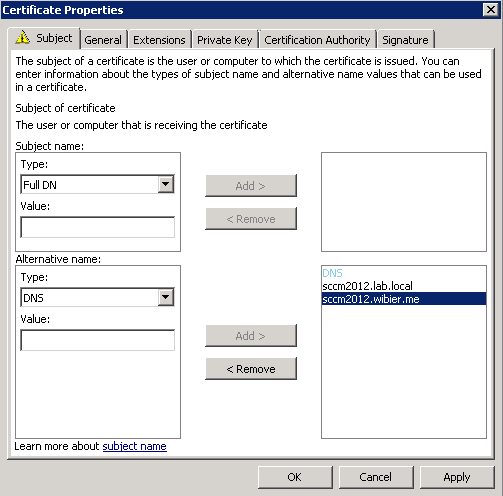
In the Certificate Properties dialog box, in the Subject tab, do not make any changes to the Subject name. This means that the Value box for the Subject name section remains blank. Instead, from the Alternative name section, click the Type drop-down list, and then select DNS.
In the Value box, specify the FQDN values that you will specify in the Configuration Manager site system properties, and then click OK to close the Certificate Properties dialog box.
Examples:
Enrollment of the ConfigMgr Web Server Certificate
Open a MMC and add the Certificate snapin for Local Computer.
Right-click Certificates and Request New Certificate. Select the ConfigMgr Web Server Certificate you created.
Select More information is required to enroll for this certificate. Click here to configure settings.
In the Certificate Properties dialog box, in the Subject tab, do not make any changes to the Subject name. This means that the Value box for the Subject name section remains blank. Instead, from the Alternative name section, click the Type drop-down list, and then select DNS.
In the Value box, specify the FQDN values that you will specify in the Configuration Manager site system properties, and then click OK to close the Certificate Properties dialog box.
Examples:
- If the site system will only accept client connections from the intranet, and the intranet FQDN of the site system server is sccm2012.lab.local: Type sccm2012.lab.local, and then click Add.
-
If the site system will accept client connections from the intranet and the Internet, and the intranet FQDN of the site system server is sccm2012.lab.local and the Internet FQDN of the site system server is sccm2012.wibier.me:
- Type sccm2012.lab.local, and then click Add.
- Type sccm2012.wibier.me, and then click Add.
 Configure IIS to use the ConfigMgr Web Server Certificate
On the SCCM Web Server open Internet Information Services (IIS) Manager.
Expand Sites, right-click your site (usually 'Default Web Site') and select Edit Bindings.
Select the HTTPS entry and Edit.
OK and Close.
(You can check the site by opening Internet Explorer and browse to your site with https://. There should not be a warning about a certificate.)
Client certificate for Distribution Points
On the Certificate Authority (CA) server open up your CA and Duplicate Template.
The template you need for this is the Workstation Authentication.
Make sure to select 'Windows Server 2003 Enterprise' as 'Windows Server 2008 Enterprise' is NOT supported by ConfigMgr 2012 SP1!
On the security tab select 'Read' and 'Enroll' for your SCCM Site Server(s), clear 'Enroll' for Enterprise Admins.
On the Request Handling tab select the Allow private key to be exported.
Back in the CA console, right-click Certificate Templates, New and Certificate Template to Issue. Choose your ConfigMgr Client Certificate for Distribution Points.
Configure IIS to use the ConfigMgr Web Server Certificate
On the SCCM Web Server open Internet Information Services (IIS) Manager.
Expand Sites, right-click your site (usually 'Default Web Site') and select Edit Bindings.
Select the HTTPS entry and Edit.
OK and Close.
(You can check the site by opening Internet Explorer and browse to your site with https://. There should not be a warning about a certificate.)
Client certificate for Distribution Points
On the Certificate Authority (CA) server open up your CA and Duplicate Template.
The template you need for this is the Workstation Authentication.
Make sure to select 'Windows Server 2003 Enterprise' as 'Windows Server 2008 Enterprise' is NOT supported by ConfigMgr 2012 SP1!
On the security tab select 'Read' and 'Enroll' for your SCCM Site Server(s), clear 'Enroll' for Enterprise Admins.
On the Request Handling tab select the Allow private key to be exported.
Back in the CA console, right-click Certificate Templates, New and Certificate Template to Issue. Choose your ConfigMgr Client Certificate for Distribution Points.
 Enrollment of the Client certificate for Distribution Points
Open a MMC and add the Certificate snapin for Local Computer.
Right-click Certificates and Request New Certificate. Select the Client certificate for Distribution Points you created.
After that Export the certificate WITH the private key.
Part 2 HERE!
Part 3 HERE!
Enrollment of the Client certificate for Distribution Points
Open a MMC and add the Certificate snapin for Local Computer.
Right-click Certificates and Request New Certificate. Select the Client certificate for Distribution Points you created.
After that Export the certificate WITH the private key.
Part 2 HERE!
Part 3 HERE!

No comments:
Post a Comment